Be cautious on the off chance that you use Facebook and furthermore have Android – and furthermore with Netflix coupons: According to the online protection master organization Zimperium, another Trojan for Android codenamed FlyTrap has reached no less than 140 nations since March 2021 and has spread to in excess of 10,000 casualties through the commandeering of informal communities, outsider application stores, and side-stacked applications.
FlyTrap
Zimperium’s zLabs Mobile Threat Research groups as of late discovered a few beforehand undetected applications utilizing Zimperium’s z9 malware motor and on-gadget recognition. After your legal examination, the not really set in stone that this beforehand undetected malware “he is important for a group of Trojans that utilization social designing stunts think twice about accounts. “
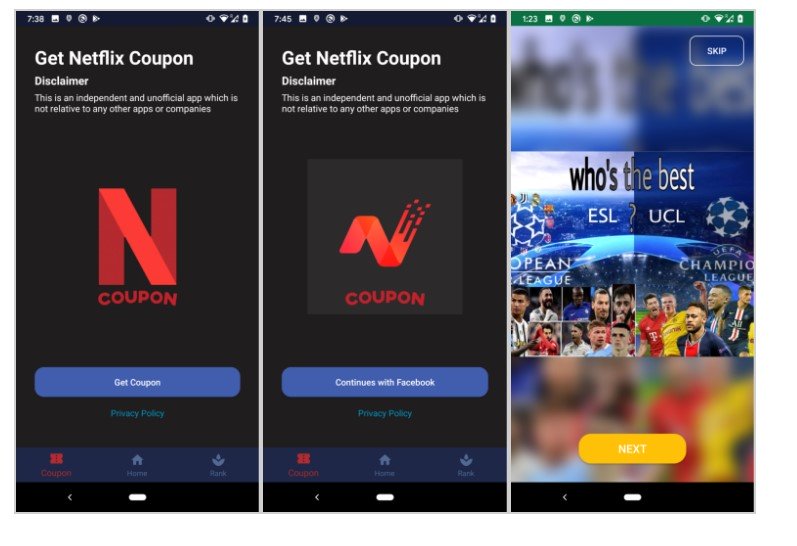
Indeed: Your Facebook account is taken. As indicated by the scientific proof of this Trojan malware for Android – immersed as FlyTrap by Zimperium-these highlights its starting point coming from a few “malignant gatherings in Vietnam that have been running this meeting seizing effort since March 2021”.
These vindictive applications were circulated “at first both through Google Play and outsider application stores “. Zimperium zLabs announced the discoveries to Google, which confirmed the examination gave and eliminated the vindictive applications from the Google Play store. In any case, these spoiled applications “They are as yet accessible in outsider advanced stores.”
The phony Netflix coupon
The portable application undermines the casualty’s social character by capturing their Facebook accounts through a Trojan that contaminates their Android gadget. Data gathered from the casualty’s Android gadget incorporates:
- ID de Facebook
- Area
- Email address
- IP address
These captured Facebook meetings can be utilized to spread malware by mishandling the casualty’s social validity through close-to-home messages with connections to the Trojan, just as dispatching publicity or disinformation crusades utilizing geolocation information of the person in question.
How does the FlyTrap Trojan work? The malware creators utilized different topics that clients would discover appealing and profoundly socially designed, for example,
- Free Netflix Coupon Codes
- Google AdWords coupon codes
- Deciding in favor of the best soccer group or player
At first accessible on Google Play and outsider stores, the application fooled clients into downloading and confiding in it with great plans and social designing. After establishment, the vindictive application shows pages that draw in the client and they ask you for an answer, similar to the ones displayed underneath.
10 casualties in 144 nations
The trickery proceeds until the client is shown the Facebook login page and requested to sign into their record to make their choice or gather the coupon code or credits. The entirety of this is simply one more stunt to trick the client, as no real coupon or casting a ballot code is created. All things being equal, the last screen attempts to legitimize the phony coupon code by showing a message that says “The coupon has terminated get-togethers and prior to spending. “
The uncovered data set contains the geolocation data of a few thousand casualties, from which the victimological map displayed underneath was produced. The Zimperium zLabs group discovered in excess of 10,000 casualties in 144 nations to date, outlining the effect of the social designing effort.


